Up until recently, it was a pain to defend againt WPA2 brute-force attacks by using a random 63-character password (the maximum in WPA-Personal) mode). Thanks to Android 10 and iOS 11 supporting reading WiFi passwords from a QR code, this is finally a practical defense.
Generating the QR code
After installing the qrencode
package, run the following:
qrencode -o wifi.png "WIFI:T:WPA;S:<SSID>;P:<PASSWORD>;;"
substituting <SSID> for the name of your WiFi network and <PASSWORD> for
the 63-character password you hopefully generated with pwgen -s 63.
If your password includes a semicolon, then escape it like this:
"WIFI:T:WPA;S:<SSID>;P:pass\:word;;"
since iOS won't support the following (which works fine on Android):
'WIFI:T:WPA;S:<SSID>;P:"pass:word";;'
The only other pitfall I ran into is that if you include a trailing newline
character (for example piping echo "..." into qrencode as opposed to
echo -n "...") then it will fail on both iOS and Android.
The full syntax for these WiFi QR codes can be found on the zxing wiki.
Scanning the QR code
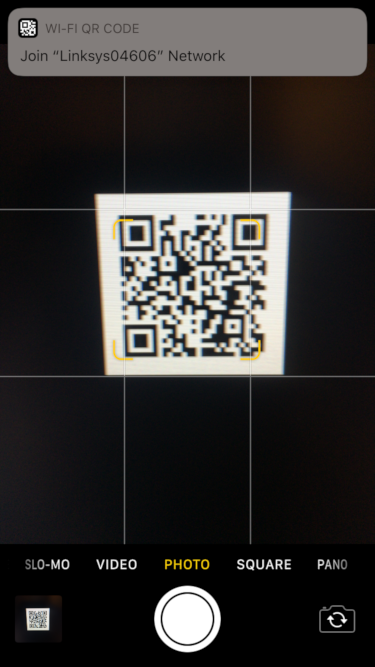
On iOS, simply open the camera app and scan the QR code to bring up a notification which allows you to connect to the WiFi network:
On Android, go into the WiFi settings and tap on the WiFi network you want to join:
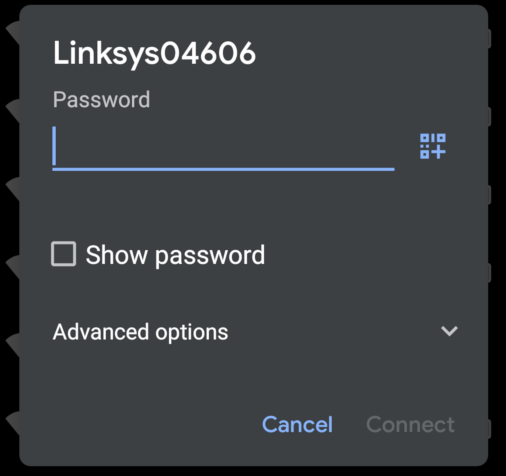
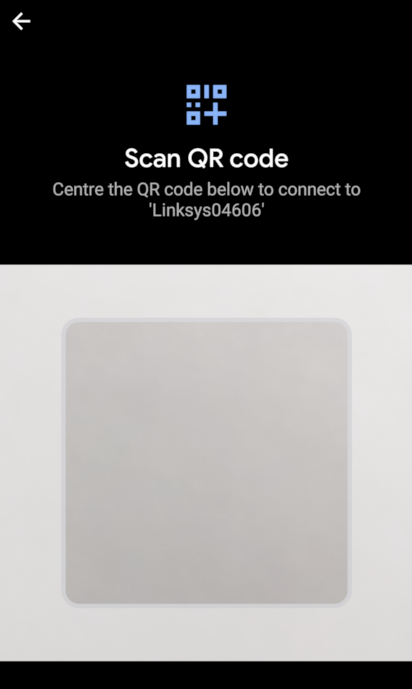
then click the QR icon in the password field and scan the code:
In-browser alternative
If you can't do this locally for some reason, there is also an in-browser QR code generator with source code available.
Wi-Fi Network config (Android, iOS 11+)
WIFI:T:WPA;S:mynetwork;P:mypass;;
Order of fields does not matter. Special characters \, ;, ,, " and : should be escaped with a backslash (). For example, if an SSID was literally "foo;bar\baz" (with double quotes part of the SSID name itself) then it would be encoded like: WIFI:S:\"foo\;bar\baz\";;